Cryptography is the art of using cryptic messages to protect and secure data in communications. The word is a derivative of the ancient Greek word kryptos, meaning hidden or secret, and graphein, meaning to study.
With the advent of information technology and the unmitigated expansion of data communications, information security is critical today. Modern cryptography deals with maintaining data authenticity & integrity and ensuring authentication & non-repudiation. The field of cryptography is vast and has enormous implementations in computer networks, e-commerce, digital fund transfer, wireless communications, military systems, etc. Modern cryptography derives from several other disciplines such as mathematics, physics, computer science, communications, electrical engineering, etc. and has become indispensable in data transfer.
Now, before we move into the details of different cryptographic techniques, let us dwell a bit into the reasons behind implementing cryptography.
Information Security Goals
Information security has three primary goals, namely, confidentiality, integrity, and availability.
Confidentiality is the most crucial objective of information security and concerns securing the information & the identity of its users. Any person and any organization would always want to protect their data from malicious individuals. Be it banking, military, or personal, data confidentiality is critical in every sector.
The aspect of confidentiality not only applies in the case of information storage but also during its transmission. We need to make sure that the data is safe throughout its life cycle.
Integrity is the term used to define the accuracy and consistency of some data properties through its life-cycle. Maintaining the integrity of data is another vital goal of any information security process. Data integrity is all about ensuring that only authorized entities can modify some data in an authorized manner.
Availability is the third component and another critical component of information security. Data is worthless unless utilized in one way or another. Denial of data service due to malicious reasons is a severe offense in cybercrime.
Malicious individuals and groups focus upon disrupting any data communication system’s above three core properties due to one agenda or the other.
So, how do cybercriminals carry out their activities, and what are the kind of attacks a system can face? Let’s get a brief look into them.
The Different Types of Security Attacks
So, how severe can information security attacks be?
If you are a computer science student, you must have dealt with network security in your computer networking assignments. Helping you learn about the myriad aspects involved in the subject they are also a significant part of your curriculum and semester score. Many universities (maybe even your own) ask their students to submit their assignments online and store them in database servers. So, you craft a perfect copy and send it to your institution’s website well within the submission deadline.
But, the following day, you are dumbstruck with horror when you learn that your college’s servers suffered from a major cyber-attack, and all data, academic & personal, were lost & compromised.
You can very well imagine the damage a malicious person can wreak by carrying out such a blatant attack.
The above situation may be hypothetical, but the risk is very much real. Numerous cyber-criminal organizations exist worldwide, and many of those receive funding from corporations, crime syndicates & even governments. Armed with the latest technology, these malicious groups carry out different kinds of attacks to disrupt systems.
Cyber-attacks can be broadly classified into two major categories: Cryptanalytic & Non-Cryptanalytic attacks.
Cryptanalytic Attacks: Cryptanalytic attacks are complicated and use a combination of statistical & algebraic techniques to determine the details of a secure cipher. The underlying mechanism of these attacks inspects the cryptographic algorithms’ mathematical properties and tries to find the distinguishers of their output distributions from uniform distributions. All cryptanalytic attacks attempt to distinguish a cipher text’s properties that do not exist in a random function.
An attacker guesses the key and then looks for its distinguishing property. If the property is detected, then the attacks successful; otherwise, the next guess is tried. Cryptanalytic attacks are theoretically successful if their guessing complexity is lower than the brute force search complexity (the analytical techniques were more manageable than the grinding deciphering methods).
Non-Cryptanalytic attacks: These kinds of attacks do not exploit the weaknesses in encrypting algorithms but are still deadly enough to compromise the three information security goals.
Cryptography aims to find ways to foil these attacks and make things impossible for beings with malicious intentions.
Cryptographic Security Techniques
Before we begin, let’s define specific terms. The original message is called plaintext, while the coded or encrypted message is ciphertext. Enciphering or encryption is converting plaintext into ciphertext, while deciphering or decryption is the opposite.
The many procedures and techniques involved in encryption & decryption constitute the field of cryptography. Besides, the methods used to decipher a message without knowing its encryption are known as cryptanalysis. The areas of cryptography and cryptanalysis are together known as cryptology.
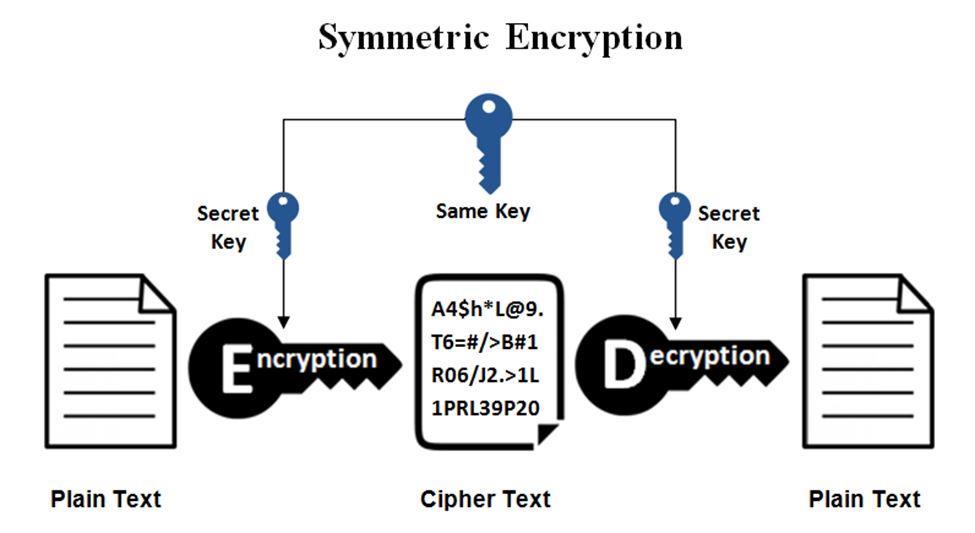
The Symmetric Cipher Model
An average symmetric encryption scheme has typically five ingredients, namely:
- The plaintext, which is the original intelligible message fed to the encryption system as raw data;
- Encryption algorithm, which performs all the transformations and substitutions on the plaintext;
- Secret Key that’s another input to the encryption algorithm. The key is independent of the plaintext and algorithm. The encryption algorithm will produce a different value every time a foreign key is used. The actions performed by the algorithm depend upon the specific key being used.
- The ciphertext is the scrambled, unintelligible message that the algorithm produces as output. A particular message and a specific algorithm will produce different ciphertexts on the application of different algorithms.
- Finally, the decryption algorithm deciphers the seemingly random ciphertext to plaintext using the secret key
Two main requirements for conventional encryption are a robust encryption algorithm and secure delivery of the secret key to both the sender and the receiver. The encryption algorithm, the plaintext, and ciphertext—none of these needs to be confidential. Only the secret key’s secrecy must be secure at all times.
THIS is the primary idea behind b and the reason behind its widespread popularity.
1. Basic Mechanism
The fact that the encryption algorithm does not need to be kept secret means that manufacturers can develop low-cost hardware implementations of encryption algorithms. Many information-processing products incorporate these encryption chips in their systems.
Let’s take a closer look at the essential elements of symmetry encryption.
A source produces a message in plaintext, X=[X1, X2, X3…XM]. The M elements of X are letters in some finite alphabet. The traditional English alphabet contains 26 capital letters, but the binary alphabet [0, 1] is now used commonly in many cases. For encryption, a key in the form K= [K1, K2, K3…KJ] is to be generated. If the key is generated at the message source, it must be sent to the destination via a secure channel. Alternatively, a trusted third party can be delegated to create the key and deliver to both the source & destination.
If the ciphertext is Y=[Y1, Y2…YN], it can be written as Y=E(K, X), where E is the encryption algorithm. The notation indicates that the ciphertext is a function of the plaintext and the secret key, while the function itself is the encryption algorithm E. With possession of key, the intended receiver uses the decryption algorithm D to decrypt the ciphertext and invert the transformation.
So, if ciphertext Y= E (K, X), then the plaintext X= D (K, Y). Now, an attacker may have access to the encrypted message, and in many cases, they even know both the algorithms.
2. Generic Decryption Attempts
If the attacker is interested in obtaining the message X, he will try to acquire the closest possible approximation X’. In some cases, the malcontent might be interested in compromising the whole encryption model and will be interested in developing the secret key K itself.
Now, most cryptographic systems are distinguished based on the type of operations used for transforming plaintext and cipher text, the number of keys used, and how the plaintext is processed.
As mentioned earlier, hackers will either use cryptanalytic techniques and brute force attacks to deduce a plaintext or the key. Whereas brute force techniques involve using every possible key on a ciphertext until a plain text is obtained, cryptanalytic practices exploit the nature of the algorithm and the characteristics of the plaintext or even some sample plaintext-cipher text pairs.
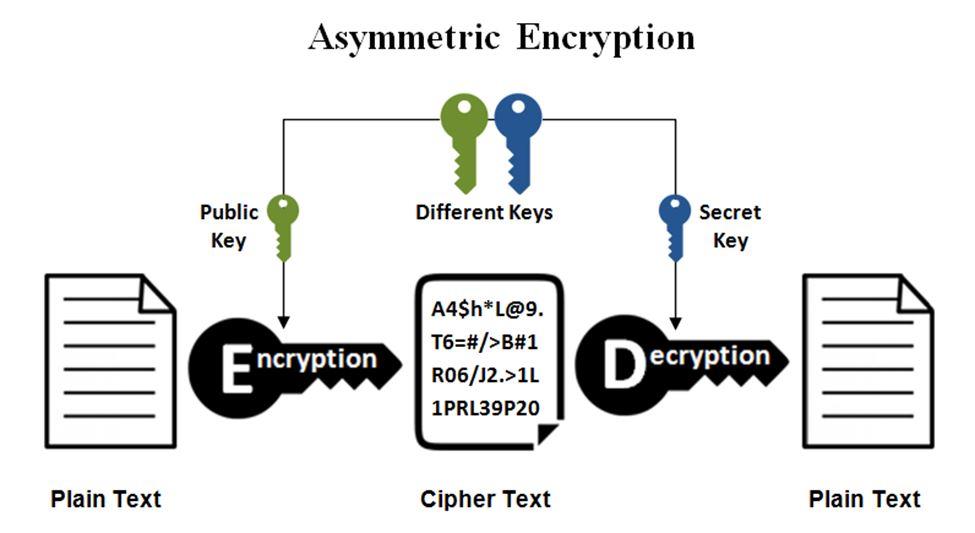
Asymmetric Cipher Model
The development of public-key or asymmetric cryptography is probably the biggest revolution in the history of cryptography. Asymmetric models move away from the general rules of substitution & permutation. Public key cryptography is based on mathematical functions and involves two separate keys, a public key, and a private key.
Now, let’s have a look at some symmetric cryptographic measures used in classical encryption processes.
Substitution Techniques in Symmetric Enciphering
The two basic building blocks of all encryption techniques are substitution and transposition. Let’s take a look at the substitution process first.
Any substitution technique replaces the letters of the plaintext with other letters, numbers, or symbols. If you consider plaintext as a sequence of bits, then the substitution will replace the plaintext bits with bits to make up the ciphertext.
Caesar Cipher
One of the earliest and most straightforward uses of a substitution cipher is in ancient Rome and done by Julius Caesar. It involved replacing every letter of the alphabet with the message three places down from the current position.
PLAIN: I will get it from the store.
CIPHER: L xloo jhw lw iurp wkh vwruh.
The Caesar Cipher’s encryption function can thus be written as C=E (3, p) = (p+3) mod 26, whereas the general Caesar’s encryption function is C=E (k, p) = (k+3) mod 26
Monoalphabetic Cipher
This particular technique utilizes permutation for arbitrary substitution. For example, we permute within the 26 letters of our alphabet, and then, there can be 26! or more than 4*1026 possible keys.
If the plaintext language is known, then its regularities and the repeating sequences in the cipher text can help deduce the plaintext equivalent.
Monoalphabetic ciphers are relatively easy to break since they reflect the frequency data of the original alphabet. Multiple substitutions for a single letter (homophones) are an ideal countermeasure in such cases. If the number of random symbols assigned to a message is equal to its frequency in the plaintext, then the single-letter frequency problem is eliminated.
Symmetric Enciphering Transposition Techniques
Transposition involves performing permutations on the plaintext. One excellent example of transposition ciphering is given below.
Say we have a plaintext “attack postponed until two am xyz.”
An apt encryption process will then be to write the message row by row, with each row having the same number of columns. Then, permute the order of columns. The order of the columns becomes the key to the algorithm.
Key: 4 3 1 2 5 6 7
Plaintext: a t t a c k p
o s t p o n e
d u n t i l t
w o a m x y z
Ciphertext: TTNAAPTMTSUOAODWCOIXKNLYPETZ
The ciphertext is read column by column, and the column sequence is the encryption key.
The field of cryptology and cryptography is vast, and even the most extensive books on the subject fail to cover all of its aspects. This article aimed to highlight the necessity of cryptography in information transfer and laid down some of the basic techniques for your knowledge.
Cryptography is an essential component for both IT management and networking assignments. Seek help from reputed services if you are struggling with the math and other principles involved in the subject.
All the best!
Thomas Grant is a chief cryptologist in a leading MNC with a master’s degree in computer applications. Hailing from South Carolina, he is a man of many parts as he writes online blogs and offers excellent computer network assignment help to students, only through MyAssignmenthelp.com.